Recommended Blogs
7 Tips on How to Secure your Web Applications

In recent years, the cyber-attacks have become rampant across computer systems, networks, websites and have been most widely attacking enterprises’ core business web applications, causing shock waves across the IT world.
These attacks can cause theft of critical data, attack networks thus reducing access to the websites or even disrupt and paralyze systems performance by restricting their access to users
- Cyber-attack facts
- Common Web Application Security Attacks
- Losses Caused due to Cyber-Security Breaches
- Sources of Cyber Security Breaches
- What is Web Application Security testing?
- Tips to Secure your Web Applications
- What are the tools for performing Web Application Security Testing?
- Conclusion
Hence, enterprises’ CXOs across the globe continue to feel the pressure due to these web application security breaches occurring more frequently. These attacks cause a lot of fraudulent activities as web applications are publicly available and are more susceptible to attacks. There are various cyber-security attacks that commonly affect web applications.
In a recent cyber-attack, earlier this month, Wikipedia went offline following a DDoS cyber attack. These attacks continue to grow and are happening more frequently
Some of the most common Web Application Security Attacks include:
– SQL Injection
– Path Traversal
– Cross-site Scripting
– Local File Inclusion
– Broken Authentication
– Misconfigured Web Servers
– Distributed Denial of Service (DDoS)
– Automated Threats
– Command Injection (CMDi)
– Web Skimming Attacks
Losses Caused due to Cyber-Security Breaches:
– Loss of critical business and customer data might lead to many adversaries
– Theft of corporate information might cause a huge impact on organizations
– At times theft of financial information might even cause economic loss to companies
– Hefty cost is incurred for repairing affected systems, networks and servers
– Major websites when hacked becomes inaccessible for end-users
– Legal complications might also occur due to cyber-attacks especially with GDPR in place for organizations in the UK and EU
– Various types of cyber-attacks can affect the interest of potential customers and seriously damage a company’s brand and reputation. -It even erodes the trust of customers
Sources of Cyber Security Breaches
– Hackers – Criminals organizations with group of people to develop attack vectors and execution vectors. – Business Competitors – Individuals creating attacking vectors with their own tools. – Industrial spies – Organized crime groups – Unhappy insiders
What is Web Application Security testing?
The practice of web application security testing helps to analyze and report on the security levels that are maintained for a web application. Enterprises of the present digital age are using web applications to make their business easily accessible for their customers. Also, these web apps have become an important need for the enterprises to communicate for achieving the business goals. While web apps provide a good number of benefits for the enterprises and the customers, the visibility of the information makes the web apps prone to cyberattacks. Therefore, to avoid such attacks for web applications, enterprises need to safeguard their apps by practicing the methods of web application security testing. However, before planning for the web application testing practice, enterprises need to check the types of web application security testing to know more.
What are the types of Web Application Security Testing?
Dynamic Application Security Testing:
DAST or the Dynamic Application Security Testing is an approach where the web app vulnerabilities, that are favorable for a hacker are identified. This method of testing helps the web app to be protected from the targets set by the hacker. Also, this practice helps to analyze how the cybercriminals can approach the system data from outside. While processing the DAST, there is no need to have access to the application’s source code; hence, the practice of DAST testing can be achieved faster.
Static Application Security Testing:
Unlike DAST, SAST looks on the vulnerabilities that can be favorable for a hacker in the web application’s source code. This set of SAST helps to analyze the byte code, binaries, design conditions, and source code so that there will not be any threat of security vulnerabilities. This way of testing makes the SAST practice popularly known as the inside-out approach.
Application Penetration Testing:
This method of security testing is an important requirement to manage regulatory frameworks. This testing practice cannot be fulfilled with automated penetration testing. Hence, it is essential for enterprises to involve manual and automated testing practices to find the vulnerabilities in the regulatory framework and also to look into issues related to business logic.
Tips to Secure your Web Applications
Enterprises can avoid such Cyber-Attacks. Listed below are 7 Tips on How to Secure your Web Applications
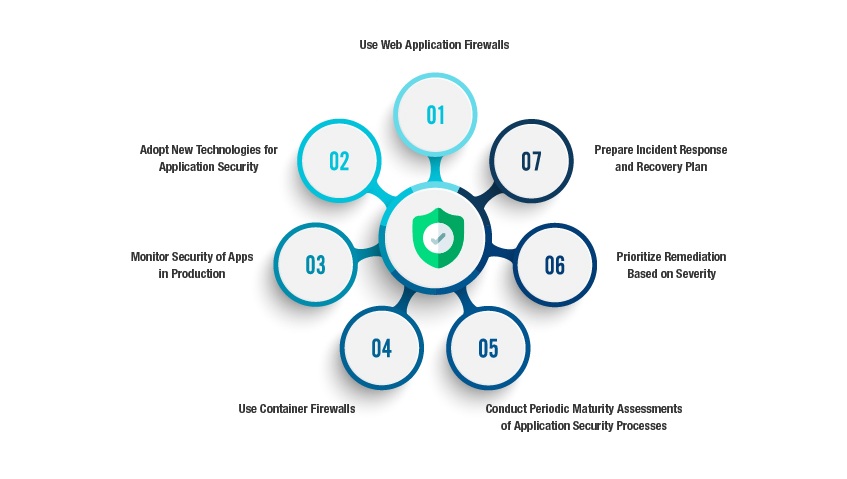
1. Use Web Application Firewalls:
Post application’s market launch, Web Application Firewalls (WAF) can be used to safeguard them from cyber-attacks. However, using WAF helps to protect against threats coming from web traffic usually within HTTP or HTTPS traffic. Some of the most common features of WAF include:
– Application attack detection – Supports common protocols – Contains logic and object formats – Supports HTTP and HTTPS by enabling SSL termination – Shows virtual patching
Moreover, effective WAPs are capable of detecting any malicious attacks and protect web applications from security risks
2. Adopt New Technologies for Application Security:
Whenever changes are made to the application with releases, the latest technology Runtime Application Self-Protection (RASP) is an effective option to be used. This approach helps to reduce human intervention and safeguard web applications from threats
3. Monitor Security of Apps in Production:
As soon as the apps are released into production, it is necessary to evaluate the behavior of the application to know the traffic patterns of users. If any suspicious activity of either high traffic or low traffic is observed, then it might be due to the influence of any possible malicious attack. More importantly, if your application generates any logs, then regular checks should be made to ensure there are no cyber-attacks in the app.
4. Use Container Firewalls:
Specific Container firewalls are used to inspect traffic within the container and help to protect the application from attacks that arise internally. Some of the components of these container firewalls are:
– Application intelligence – Cloud-native – Whitelist and Blacklist based regulations – Integration and management with containers – Compatibility with CICD (Continuous Integration and Continuous Development) – Container threat protection – Container specific packet analysis Thus, using container firewall ensures to inspect intrusions in all traffic within and outside the container. They help to protect the workloads, application services and stacks during the run-time. Implementation of container firewall technology will be the best practice to keep the container environments safe from attacks.
5. Conduct Periodic Maturity Assessments of Application Security Processes:
There are certain tools offered by Open Web Security Project (OWASP) which should be used to assess the Software Assurance Maturity Model. These tools help to deliver a comprehensive check for testing the security of your web applications and ensures that no vulnerabilities are left during the testing process
6. Prioritize Remediation Based on Severity:
Whenever a security vulnerability is identified, prioritization of its remediation should be taken up quickly. Based on the severity of vulnerabilities, they should be fixed within a specified time frame such that business risk is minimized
7. Prepare Incident Response and Recovery Plan:
Enterprises should be prepared for web application security breaches and hence should plan ahead to handle them. The various phases of the Incident Response Plan include Identification, Containment, Eradication, Recovery and Post Incident Activity.
-> The initial Identification phase should include finding out all security breaches such as XSS attack, LDAP injection, failure to restrict URL access, SQL injection attack or OS command injections
-> The Containment phase includes steps to mitigate the impact of incidents on various targeted environments
-> Disaster recovery plans should be effectively made in the Eradication phase to replace the hacked or defaced page with a clean page and use anti-virus tools, change passwords (if any) or uninstall OS as per need. This Eradication phase is a priority and if the application is made available to the end-users without eradicating various threats, then it might also affect the brand, customer loyalty and cause significant economic losses
What are the tools for performing Web Application Security Testing?
1. Zed Attack Proxy (ZAP): -The Open-source and multi-level platform tool is developed by the Open Web Application Security Project (OWASP) -This tool is used to find vulnerabilities in web applications during the development and testing phase
2. W3af: -This tool is a popular web application security testing automation framework -Allows to test over 200 types of web application’s security issues
3. Kiuwan: -This tool is successful to work for OWASP, SANS 25, CWE, HIPA and more -Integrating Kiuwan in IDE helps to achieve faster feedbacks in development -This tool supports major of programming languages and integrates with DevOps tools
4. Grabber: -This tool is designed to scan small web applications -A range of vulnerabilities such as verification of file backups, cross-site scripting, AJAX verification, SQL injection, etc.
5. SonarQube: -This is an open-source security testing tool, that can integrate with continuous integration tools -It is used for measuring the quality of the source code -This tool is capable to perform analysis for 20+ programming languages
Conclusion:
Enterprises should take measures to mitigate cyber-attacks by adopting proper measures such as protecting the systems with anti-virus, time-to-time OS updations, configuring firewalls to allow only specific trusted ports and hosts that are required along using password protection
It is critical to follow a cyber-security incident response plan and risk management plan to overcome cyber threats and vulnerabilities
Evidently, CXOs need to leverage web application security testing and penetration testing to overcome the possible attacks on their business applications and systems
Connect to our security testing experts for a quick security evaluation of your business application/system.
Discover more
