Recommended Blogs
What are DDoS attacks and How to Mitigate them
Cyber-attacks continue to shake the IT world across industries and domains, collapsing critical applications, paralyzing traffic and networks of systems.
There are many types of cyber-attacks and some of the most common are:
– Man-in-Middle attack – Phishing – Drive-by attack – Password attack – SQL Injection attack – Cross-word scripting attack – Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks (the most severe among all)
These continue to cause huge economic losses to organizations and businesses. The CXOs across businesses continue to be perplexed with these attacks and have to bear huge economic losses (even in the form of bitcoins) and network inaccessibility leading to loss of brand reputation.
What are DoS and DDoS Attacks?
DoS attack specifically is an attack by hackers wherein they use a computer or a set of computers to flood a server with TCP and UDP packets thus preventing users to have no access to their service.
A DDoS attack occurs when multiple systems try to attack the target system and finally succeed it by blocking their traffic and subsequently those systems become inaccessible to the users. Moreover, the targeted network is then attacked with a sudden influx of packets from numerous locations, thus leading to the attacked systems going offline for a particular period of time.
The larger the attack, it becomes difficult for businesses to recover. Interestingly, all DDoS attacks are DoS attacks but not all DoS attacks are of DDoS type.
Major types of DDoS Attacks:
– Volumetric attacks: These attacks usually make use of high traffic to influence the bandwidth of the network and measures the magnitude in bits per second (Bps). These include ICMP floods, spoofed-packet floods, UDP floods, etc. – Protocol attacks: These attacks intake server resources or exploit the communication equipment such as load balancers and firewalls. These include smurf DDOS, fragmented packet attacks, SYN floods, etc. Also, the attacks are measured in packets per second (Pps). – Application layer attacks affecting web servers (most common): These attacks are the most dangerous of all the types as these try to crash the web applications/servers with simple requests. The magnitude of these attacks is measured in Requests per second (Rps). These include GET/POST floods, attacks that target Windows, Apache, etc.
Most common forms of DDoS attacks:
– UDP Floods: A large volume of User Datagram Protocol (UDP) packets are sent to a targeted system to exploit the response and device ability. – ICMP (Ping) Flood: In Internet Control Message Protocol (ICMP) attack, devices get influenced by the attackers with ICMP echo-requests. – SYN Flood: This type of attack aims to consume the server resources to make the server unavailable to the regular traffic. – Slowloris: In this attack, a machine takes down the properties of another web server without affecting the ports and other services on the target network. – NTP Amplification: The Network Time Protocol (NTP) is a reflection-based volumetric DDoS, where an attacker exploits the functionality of the NTP server of a targeted network. – HTTP Flood: It is a type of volumetric DDoS attack that influences a targeted server with HTTP requests. The attack is effective when the application/server is forced to allocate the maximum responses to every request. – Zero-Day Attacks: This is a very powerful and dangerous attack as the software security flaw will be known by the software developer but doesn’t have the scope to fix the attack. The complete potential of the software will be under the control of the cybercriminal.
Why DDoS Attacks Occur?
There are various reasons why these cyber-attacks occur but they preferably try to attack enterprises in hope of some ransom (Extortion) in a way to extort money from them.
Malicious competitors might also be a reason for causing these types of attacks where they might grab your customers by placing your network down. Some of the others are Hacktivism, Causing Trouble, Boredom, or might even be due to Disgruntled Employees.
These attacks mostly occur after identifying a vulnerability observed by hackers. At times, cybercriminals use automated bots to keep track of vulnerable websites and thus attack them. It has been a scaring fact to know that about 86% of web applications have at least one vulnerability and might have a chance for cyber-attack.
Challenges faced with DDoS attacks:
– The attacked systems become inaccessible to users
– There could be loss of critical user data or any other important business data
– Blocks e-commerce sites if attacked and stops transactions
– Affects brands and companies by causing economic loss
– Holds your actions on the site for a specific period of time and causes networks and system’s malfunctioning
Some Recent DDoS Attacks:
1. According to a recent report, In a statement, Wikipedia parent company Wikimedia confirmed the site had been hit by a “malicious attack that has taken it offline in several European countries for intermittent periods,” with the company’s German Twitter account said its server was “paralyzed by a massive and very broad DDoS attack (Sept 2019) 2. The number of DDoS attacks detected by Kaspersky jumped 18% year-on-year in the second quarter i.e. Q2 2019, according to the latest figures from the Russian AV vendor 3. In June 2019, a powerful DDoS attack hit Telegram. The attack was carried out primarily from Chinese IP addresses. 4. A rise in multi-vector DDoS attacks has caused traffic congestion by flooding networks with numerous illegitimate network packets. 5. In April 2019, a DDOS attack was hit by one of the clients of Imperva with 580 million packets per second. This is the largest DDOS attack in recent times. 6. In February 2018, the largest DDOS attack was recorded for the GitHub Company in that year. The company had to experience 1.35 terabits of traffic was overseen by the servers with 126.9 million PPS. As per the statements of GitHub, the traffic made the GitHub’s system down for 20 minutes. 7. In March 2018, the leading business assurance provider, NETSCOUT stated that its DDOS threat detection system and Arbor ATLAS global traffic was confirmed with a threat and it resulted in 1.7 Tbps Memcached. 8. In the second half of the year 2017, Square Enix’s Final Fantasy XIV – an online role-playing game was attacked with a DDOS via botnets. The attack was spanned for the summer and then the other set of attacks was seen during the fall.
Markets and Markets, a leading market firm, states that the DDoS protection and mitigation market is expected to grow to $4.7 billion by 2024, up from $2.4 billion this year 2019. The report also shows that small and medium businesses have become their major targets due to their existing gaps and vulnerabilities in their systems.
How to mitigate DDoS Attacks:
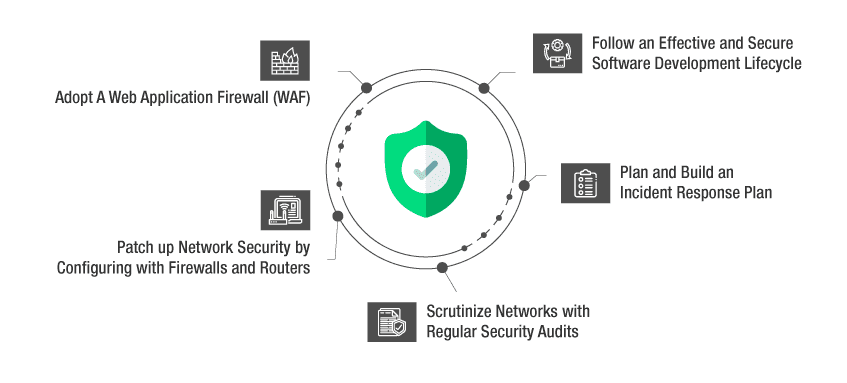
1. Adopt A Web Application Firewall (WAF):
Firewalls are the best way to protect the HTTP traffic between an application and the internet. In situations wherein a cybercriminal or a hacker targets a DDoS attack, WAF blocks all malicious attacks on the application. Specifically, WAF blocks malicious HTTP traffic before it reaches the actual site. Certain policies can be formulated to determine which IP addresses could be blacklisted or which of the IP addresses should be whitelisted using WAF.
2. Patch up Network Security by Configuring with Firewalls and Routers:
There are many entry points into the networks that should be blocked by using configurable firewalls and routers. If a firewall is used, it helps in detecting the IP addresses that attack while routers have DDoS protection settings and filters that can be used to control access of protocols.
3. Scrutinize Networks with Regular Security Audits:
Frequent network security audits should be conducted by organizations, and it should be mandated to follow these audits. The strength of the password should be followed and software updates should be taken up across systems periodically. These security audits help to reveal how vulnerable is the organization’s network to threats!
4. Plan and Build an Incident Response Plan:
In order to protect your network and applications from cyber-attacks, it is important to develop an incident response plan that details various technologies and protocols necessary to protect from DDoS attacks.
5. Follow an Effective and Secure Software Development Lifecycle:
While the application is still in the development phase, it is essential to embed cyber-security options as a core component of SDLC. Most of the apps continue to be an easy point for hackers post-production, and hence it is essential to follow several SDLC protocols to protect applications from these attacks.
Conclusion:
Businesses should take up the right protective measures to safeguard applications using (WAF) firewalls. It is essential to be pro-active and be ready with a well-defined incident response plans to mitigate any possible cyber-attacks and protect your network and applications from them. Loss of critical data, inaccessible network, damage to brand reputation should be mitigated by embracing web application security testing from QA security testing experts.
Discover more

