Recommended Blogs

Security Testing – An Effective Guide for Businesses
Table of Content
- What is Security Testing?
- Why Do Businesses Need Security Testing?
- Recent Cyber-Attacks : Why Robust Security Testing Is Essential
- Different Types of Cyber Threats Businesses Should Know
- What Are the Various Security Testing Methods Businesses Can Leverage
- Important Techniques Used in Security Testing
- How Is Security Testing Performed in Parallel to the SDLC?
- Role of Security Testing in the DevOps Environment
- Benefits of Embedding Security Testing into the DevOps Environment
- Who Performs Security Testing?
- Best Security Testing Practices to Ensure Robust Cybersecurity in 2026
- Upcoming Cybersecurity Threats and Trends to Watch in 2026
- Security Testing Tools Businesses Should Leverage
- Conclusion
Cyber threats are rising sharply, and every organization, large or small, local or global, is a potential target. The shift to remote and hybrid work has made company networks, devices, and data more exposed than ever before.
For today’s businesses, cybersecurity isn’t just an IT issue—it’s essential to safeguarding their reputation, operations, and client trust. A proactive approach, including regular security testing, helps them identify and address vulnerabilities before attackers can exploit them. Skipping this step can lead to costly breaches, downtime, and regulatory penalties.
What is Security Testing?
Security testing is the process of evaluating a system, application, or network to identify vulnerabilities, misconfigurations, or weaknesses that could be exploited by cyber threats. It plays a critical role in ensuring that digital assets are resilient against unauthorized access, data breaches, and other forms of malicious attacks.
This testing technique involves various approaches such as penetration testing, vulnerability scanning, security audits, and risk assessments, all aimed at detecting and addressing potential security flaws before they can be exploited. The goal is to assess how well a system maintains confidentiality, integrity, availability, authenticity, and resilience.
Security testing is essential for protecting sensitive data, maintaining regulatory compliance (e.g., GDPR, HIPAA, PCI DSS), and building user trust by ensuring that applications and infrastructure are secure by design. Whether integrated into the Software Development Life Cycle (SDLC) or implemented as part of DevSecOps practices, security testing helps businesses reduce risk exposure and strengthen their overall cybersecurity posture.
Why Do Businesses Need Security Testing?
Security testing is essential for modern organizations that want to protect data, maintain trust, and ensure seamless business operations.
Here’s why it matters:
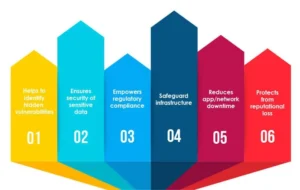
-
Identifies Hidden Vulnerabilities
Security testing uncovers weaknesses in software, applications, and systems that might not be visible during regular development or functional testing. These hidden vulnerabilities, if missed, can become easy targets for attackers.
-
Ensures the Security of Sensitive Data
By proactively testing for risks, organizations safeguard sensitive customer and business data against unauthorized access, leaks, or theft. This protects both users and the brand.
-
Empowers Regulatory Compliance
Many industries require strict adherence to data protection laws and standards. Security testing ensures systems are compliant, helping businesses avoid fines and reputational harm from regulatory breaches.
-
Safeguards IT Infrastructure
Testing goes beyond individual applications to cover the entire IT environment. It helps defend networks, servers, and endpoints from new and evolving cyber threats.
-
Reduces Application and Network Downtime
Cyber-attacks can disrupt core business functions, leading to costly outages. Regular security testing minimizes the risk of such interruptions, protecting business continuity and enhancing customer experience.
-
Protects Against Reputational Loss
A major breach can erode customer trust and damage a company’s reputation. Security testing helps mitigate these risks, preserving both revenue and brand value.
Recent Cyber-Attacks : Why Robust Security Testing Is Essential
- United Natural Foods Inc. (UNFI) Supply Chain Attack (June 2025): A major cyberattacks disrupted United Natural Foods Inc.’s ordering and delivery systems, creating grocery shortages throughout North America and exposing supply chain vulnerabilities.
- Marks and Spencer (M&S) Ransomware Attack (April–May 2025): UK retailer M&S experienced a ransomware incident that impacted its deliveries and payments, emphasizing that retail giants remain top cyber targets.
- Oracle Cloud Data Breach (March 2025): Attackers exfiltrated 6 million records from Oracle Cloud, exposing encrypted passwords, keys, and configuration files of more than 140,000 users.
- Episource Healthcare Data Breach (June 2025): A ransomware incident at Episource resulted in the theft of medical data belonging to 5.4 million US patients, underscoring healthcare’s continued risk from cyber threats.
- Massive DDoS Attack Defended by Cloudflare (May 2025): Cloudflare mitigated a record 7.3 Tbps DDoS attack—one of the largest ever, targeting a global hosting provider, generated from over 122,000 IP addresses.
Different Types of Cyber Threats Businesses Should Know
Modern organizations face a wide range of cyber threats, each targeting different aspects of their digital environment. Understanding these threats is essential for building effective security strategies. Here are the most common types businesses should be aware of:
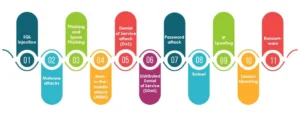
- SQL Injection: Attackers inject malicious SQL code into input fields on database-driven websites, allowing unauthorized access to sensitive data or manipulation of the backend database.
- Malware Attacks: Malicious software, such as viruses, ransomware, trojans, or spyware, is silently installed on a system to damage, steal, or manipulate data without the user’s consent.
- Phishing and Spear Phishing: Cybercriminals send deceptive emails that resemble messages from trusted sources, tricking recipients into revealing confidential information or triggering malicious actions. Learn about the most common cyber attack forms.
- Man-in-the-Middle Attack (MitM): An attacker secretly intercepts and potentially alters the communication between two parties—like a client and a server—often to eavesdrop or impersonate a trusted entity.
- Denial of Service (DoS) Attack: The perpetrator overwhelms a system or network with excessive requests, making it inaccessible to legitimate users.
- Distributed Denial of Service (DDoS): A large volume of traffic from multiple compromised sources floods an organization’s resources with fake or automated requests, causing service outages or significant slowdowns. See how to mitigate DDoS attacks.
- Password Attack: Attackers use various techniques, such as brute-force, credential stuffing, or even physical observation, to obtain user passwords and gain unauthorized access.
- Botnet: A network of malware-infected devices, controlled remotely by cybercriminals (“bot herders”), can be leveraged to launch large-scale attacks such as DDoS, data theft, or credential harvesting.
- IP Spoofing: By falsifying the sender’s IP address in data packets, attackers make their traffic appear legitimate, allowing them to bypass some security measures or execute further attacks.
- Session Hijacking: Attackers take control of a legitimate user session, typically after log-in, to steal sensitive information or perform unauthorized actions on behalf of the user.
- Ransomware: Files or systems are encrypted by attackers who then demand payment to restore access, often bringing business operations to a standstill until the ransom is paid.
What Are the Various Security Testing Methods Businesses Can Leverage
- Static Application Security Testing (SAST): A white-box testing approach, SAST analyzes source code, bytecode, or binaries for vulnerabilities early in the development lifecycle. It helps catch issues before code is deployed, reducing remediation cost and effort.
- Dynamic Application Security Testing (DAST): A black-box technique, DAST tests running applications from the outside in—simulating attacks a hacker might attempt. It is ideal for detecting runtime vulnerabilities, such as injection flaws and authentication issues.
- Interactive Application Security Testing (IAST): Combines static and dynamic methods by using software agents to monitor applications in real time during functional testing. IAST provides continuous, context-aware feedback, helping identify vulnerabilities as code executes.
- Red Team Assessment: Advanced, goal-oriented exercises where experts emulate sophisticated adversaries. Red teaming tests a business’s detection and response capabilities, not just its technical defenses.
- Penetration Testing (Ethical Hacking): Security professionals simulate real-world attacks to uncover exploitable weaknesses across software, networks, and infrastructure. Learn more in our Penetration Testing Guide.
- Risk-Based Testing: Risk-based testing focuses resources on the most critical assets and the highest-impact threats, ensuring testing delivers maximum business value.
- Security Review: A holistic audit of security policies, configurations, DevOps practices, and organizational procedures—validating that best practices are followed across your software and delivery pipelines.
- Software Composition Analysis (SCA): Scans third-party and open-source components for known vulnerabilities, ensuring that external libraries and dependencies are safe and up to date—an essential step for modern, component-driven applications.
Important Techniques Used in Security Testing
Effective security testing involves targeted techniques that uncover common and emerging vulnerabilities in modern applications.
Here are some essential methods used by professionals:
Testing for SQL Injection
Testers attempt to inject malicious SQL queries into application input fields to check if databases are susceptible to unauthorized access, data leaks, or manipulation. Input validation and parameterized queries are crucial defenses.
Cross-site Scripting (XSS) Checks
The goal here is to determine if the application lets attackers inject and execute scripts in the browser of other users. Testers attempt to submit HTML or JavaScript code to fields such as forms or search boxes, ensuring scripts cannot be rendered and executed in the application context.
Session Management Testing
Testers inspect how user sessions are handled—verifying that sessions expire after suitable inactivity or total duration, and that session cookies are properly scoped (e.g., HttpOnly, Secure, SameSite flags) to prevent hijacking.
Password Cracking Simulations
Ethical testers use common username/password combinations and password-cracking tools to check if user credentials are easily guessable, reused, or poorly stored. They may also attempt brute-force attacks, checking if account lockout protections exist.
Security Misconfiguration Checks
The team examines configuration settings for weaknesses, such as the use of default passwords, outdated software, unnecessary features or services, and unprotected files, endpoints, or databases—ensuring all are secured according to best practices.
Sensitive Data Exposure Testing
Applications are reviewed to confirm that sensitive data—such as credit card numbers, health records, or personal information—is properly encrypted, masked, and inaccessible to unauthorized users or processes.
Unvalidated Redirects and Forwards
Security testers try to manipulate redirection or forwarding mechanisms within the application to see if users can be sent to untrusted, potentially malicious destinations. Robust applications restrict or validate redirection targets to prevent data theft.
How Is Security Testing Performed in Parallel to the SDLC?
Integrating security testing into every stage of the Software Development Life Cycle (SDLC) is widely recognized as a best practice for modern, resilient application development. This approach—often called “Shift Left”—ensures that vulnerabilities are identified and addressed early, reducing cost, complexity, and business risk.
Here’s how security testing aligns with each phase of the SDLC:
-
Requirements Gathering
Security professionals review business goals and regulatory obligations and conduct initial risk assessments. This early analysis helps define security requirements, threat models, and baseline protections right from the start.
-
Design
Testers and architects collaborate to plan security test cases and select controls appropriate for the proposed system architecture. This includes designing for secure authentication, authorization flows, encryption, and secure data handling.
-
Coding
As developers write code, testers carry out white-box testing techniques like Static Application Security Testing (SAST) and Software Composition Analysis (SCA). These automated tools scan source code and third-party libraries for vulnerabilities, insecure practices, and outdated components before the code becomes part of the live product.
-
Testing
During formal QA, teams conduct Vulnerability Assessment and Penetration Testing (VAPT) using both manual and automated approaches. Dynamic Application Security Testing (DAST) and Interactive Application Security Testing (IAST) simulate attacks on running applications, uncovering runtime flaws and weaknesses in real business use cases.
-
Operations & Maintenance
After deployment, testers continually monitor for new vulnerabilities, perform regular impact analysis, and conduct ongoing security reviews. This phase may include periodic penetration tests, patch validation, and real-time monitoring for threats as the environment evolves.
Key Principles:
- Start security testing as early as possible—don’t wait for development to finish.
- Use both automated tools and manual analysis for comprehensive coverage.
- Integrate security checks into CI/CD pipelines for continuous validation.
- Maintain security as an ongoing, iterative process throughout application maintenance.
Adopting this parallel, lifecycle-wide strategy helps organizations reduce the risk of late-stage surprises, control costs, and deliver software that’s both high quality and robustly secure.
Role of Security Testing in the DevOps Environment
Security testing is fundamental to a successful DevOps environment, helping organizations ensure security is built into every stage of the CI/CD pipeline—not bolted on at the end. This integrated approach, often called “DevSecOps,” transforms security from a final checkpoint to a continuous, collaborative process.
Here’s how security testing fits into each phase of the DevOps lifecycle:
1. Planning Phase
At the outset, the DevSecOps team works with business stakeholders to define security requirements, set clear policies, and outline risk management strategies. This early alignment ensures that security is a foundational part of the development process.
2. Coding Phase
Developers and testers collaboratively conduct code reviews and apply secure coding standards to minimize vulnerabilities as code is written. Early evaluation helps catch issues before they progress further down the pipeline.
3. Build Phase
Here, automated tools perform Static Application Security Testing (SAST) and dependency scans to identify vulnerabilities in both custom code and third-party libraries before the software is packaged for deployment.
4. Testing Phase
Security testers run Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and targeted penetration tests. These methods simulate real-world attack scenarios on running applications to uncover and remediate security weaknesses.
5. Release Phase
The software is validated against security policies, compliance guidelines, and industry best practices. Continuous and automated testing at this stage ensures that no critical risks or bugs remain as code progresses toward production.
6. Operations Phase
Security extends beyond application code to the infrastructure itself. Using Infrastructure as Code (IaC), configuration management, and secrets management, organizations ensure secure, repeatable environment provisioning and protect sensitive credentials.
7. Monitoring Phase
Real-time logging, automated alerts, and threat intelligence solutions monitor applications and infrastructure for unusual activity or emerging vulnerabilities. Efficient vulnerability disclosure and response processes help organizations address new threats proactively.
Benefits of Embedding Security Testing into the DevOps Environment
Integrating security testing throughout the DevOps pipeline offers organizations a range of key advantages:
- Early Bug and Vulnerability Detection: Potential security issues are identified and resolved early in the development cycle, minimizing downstream risks and rework.
- Safer, Resilient Software: Security checks at every stage ensure that delivered software is robust and less likely to be compromised in production.
- Reduced Costs and Losses: Catching and fixing vulnerabilities early lowers the expense and business impact of breaches, downtime, and last-minute remediation.
- Accelerated, Secure Releases: Automated security testing streamlines workflows, allowing for faster and more frequent releases while maintaining a strong security posture.
- End-to-End Transparency: Embedding security ensures clear visibility across the software lifecycle, supporting better decision-making and accountability from the start.
- Faster Recovery from Incidents: With security processes in place, organizations can respond and recover quickly from attacks or vulnerabilities that do occur.
- Continuous Compliance: Ongoing security checks help maintain compliance with industry regulations and standards throughout the delivery pipeline.
- Greater Agility: Teams can respond rapidly to new threats or changes in requirements without compromising security.
- Improved Customer Trust and Brand Value: Demonstrated commitment to security builds user confidence, strengthens customer relationships, and enhances brand reputation.
Who Performs Security Testing?
Security testing is carried out by specialized professionals, each bringing different expertise depending on an organization’s IT landscape and security needs:
- Penetration Testers (Pen Testers/Ethical Hackers): Also known as “white hats,” these experts are trained to conduct authorized, simulated cyber-attacks on applications, networks, and infrastructure. Their goal is to find and safely disclose vulnerabilities before real attackers do—helping businesses prevent financial and reputational damage.
- Security Test Engineers: These professionals design, execute, and automate security tests throughout the development and operations lifecycle. They work closely with development and DevOps teams to integrate security checks into the software pipeline.
- Security Audit Teams: Typically part of an internal risk and compliance group or a third-party firm, these teams review security policies, configurations, and controls. They ensure procedures meet industry regulations and best practices.
- Cybersecurity Testing Managers: They oversee the entire security testing process, coordinate between technical and business teams, and ensure alignment with security objectives and compliance requirements.
- Red Team/Blue Team Members: In large or advanced organizations, dedicated “Red Teams” simulate targeted attacks while “Blue Teams” focus on defense and response. This approach tests both detection and resilience.
Key Takeaway: The complexity of today’s IT environments requires collaboration among multiple roles—penetration testers, security engineers, audit specialists, and managers—to build a comprehensive and robust security posture. Choosing the right mix of experts ensures all aspects of your infrastructure are assessed and protected.
Best Security Testing Practices to Ensure Robust Cybersecurity in 2026
As cyber threats continue to evolve in sophistication and scale, businesses must adopt advanced security testing practices to protect critical data and maintain resilience. Here are key best practices for 2026:
- Adopt End-to-End Data Encryption: Encrypt sensitive data both at rest and in transit using strong algorithms like AES-256 and TLS 1.3. Encryption remains a fundamental defense to safeguard information against interception, tampering, and theft.
- Implement Continuous Data Backup and Recovery Strategies: Use automated, frequent backups with immutable storage and tested disaster recovery plans. Cloud and hybrid backups ensure rapid recovery from ransomware attacks and data corruption incidents.
- Enforce Multi-Factor Authentication (MFA) with Passwordless Options: Expand beyond traditional MFAby adopting passwordless authentication methods (biometrics, FIDO2 tokens) that enhance security while improving user experience.
- Use AI-Driven Password and Credential Management: Employ AI-powered tools that detect weak, reused, or compromised passwords and enforce dynamic access controls. Integrate with Identity and Access Management (IAM) systems for real-time risk scoring.
- Secure Remote and Hybrid Access: Leverage Zero Trust Network Access (ZTNA) principles instead of relying on perimeter defenses. Enforce strict device posture checks and continuous authentication across all access points, including public networks.
- Deploy Advanced Endpoint Protection and Extended Detection and Response (XDR): Use next-gen antivirus combined with XDR for proactive threat hunting and automated containment of malware and advanced threats.
- Integrate Security Testing Throughout the SDLC and DevOps Pipelines: Continuously run Static (SAST), Dynamic (DAST), Interactive (IAST), and Software Composition Analysis (SCA) with automation for early and rapid identification of vulnerabilities.
- Conduct Regular Red Team Exercises and Automated Penetration Testing: Combine manual and AI-assisted simulations to test real-world attack scenarios and strengthen detection and response capabilities.
- Monitor Threat Intelligence and Vulnerability Feeds Real-Time: Stay informed on emerging threats and zero-day vulnerabilities by integrating real-time intelligence into security testing and operational controls.
- Emphasize Security Awareness and Social Engineering Resilience: Regularly train employees on the evolving threat landscape, including AI-driven phishing and deepfake scams, to reduce human risk factors.
By implementing these updated practices, businesses will be better positioned to defend against the increasingly complex cyber threats of 2025, ensure regulatory compliance, and maintain operational resilience.
Upcoming Cybersecurity Threats and Trends to Watch in 2026
As the digital landscape rapidly evolves, organizations must stay informed about emerging cyber threats and security trends to protect their assets and reputation.
Here are the most critical trends and risks shaping cybersecurity in 2026:
1. AI-Driven Cyber Attacks
Attackers are using artificial intelligence to automate phishing, create persuasive deepfakes, and mutate malware faster than legacy defenses can adapt. Over 8 million AI-generated deepfakes are circulating online in 2025, amplifying risks of fraud and identity theft.
2. Advanced Ransomware and Extortion
Ransomware incidents have more than doubled compared to 2024. Attackers now use double and triple extortion tactics—encrypting data, threatening public leaks, and even targeting business partners if ransoms remain unpaid. Healthcare, finance, and supply chain sectors are particularly affected.
3. Cloud Security Challenges
Widespread adoption of multi-cloud and hybrid solutions has increased the chance of misconfigurations, exposed APIs, and third-party breaches. 32% of business cloud assets were found neglected in recent industry audits, with more than 76% having at least one public-facing vulnerability.
4. Soaring IoT and Connected Device Risk
With nearly 20 billion IoT devices connected globally in 2025, unsecured endpoints offer attackers new ways to breach networks, conduct DDoS attacks, or steal data. The manufacturing, healthcare, and infrastructure sectors are most impacted by these threats.
5. Zero Trust Becomes Standard
Traditional network perimeters are vanishing with remote work and cloud expansion. Businesses are moving to Zero Trust models, deploying continuous identity verification and strict access controls to limit attacker movement inside the network.
6. Social Engineering and Deepfake Phishing
AI-powered social engineering—using fake voices, videos, or highly targeted phishing—has become more convincing than ever. Business email compromise (BEC) and impersonation scams are targeting employees and executives across industries.
7. Third-Party and Supply Chain Vulnerabilities
Attacks on software vendors and service providers have surged, with supply chain breaches nearly doubling year over year. Effective risk management now requires continuous vetting and monitoring of partners, not just internal controls.
8. Preparing for Quantum Threats
Organizations are starting to invest in quantum-resistant cryptography, anticipating future threats where quantum computers could decrypt today’s secure communications.
Key Takeaway: Defending against 2026’s threats means adopting AI-driven security, embedding Zero Trust, proactively testing for cloud and IoT risks, continuous monitoring, and regular employee training. Staying informed and agile is crucial—only a proactive strategy can keep pace with the evolving cyber risk landscape.
Security Testing Tools Businesses Should Leverage
Choosing the right security testing tools is crucial for identifying vulnerabilities, automating assessments, and ensuring the robustness of your software and infrastructure.
1. Veracode
A cloud-based platform offering a complete suite of security tests—including Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), Software Composition Analysis (SCA), and on-demand penetration testing. Veracode integrates seamlessly with CI/CD pipelines and provides detailed remediation guidance for developers.
2. Acunetix
An end-to-end web application security scanner designed to quickly identify vulnerabilities such as SQL Injection and Cross-site Scripting. Acunetix features DeepScan Technology, a Login Sequence Recorder (LSR) for authenticating into complex sites, AcuMonitor for detecting out-of-band vulnerabilities, and AcuSensor for deeper code analysis—offering comprehensive automated and interactive testing.
3. Burp Suite Professional
Widely adopted by security professionals for manual and automated web application penetration testing. Burp Suite acts as an intercepting proxy, enabling detailed inspection and manipulation of browser traffic. Its tools help discover vulnerabilities, automate repetitive scanning, and accelerate the process of securing web-based platforms.
4. Micro Focus Fortify
A comprehensive suite supporting enterprise-grade application security. Fortify covers dynamic and static testing, DevSecOps enablement, cloud security, and software supply chain risk management. Components include Fortify on Demand (cloud testing), Static Code Analyzer, Software Security Scanner, WebInspect (for DAST), and integrated Software Composition Analysis to cover every stage of the SDLC.
Why These Tools? These solutions are recognized for their accuracy, scalability, and integration capabilities—making them ideal for organizations aiming to embed security into their development lifecycle, support digital transformation, and maintain compliance with industry standards.
Conclusion
As businesses continue their digital transformation, the volume and sophistication of cyber-attacks keep rising. Ensuring robust security for applications, data, networks, systems, and infrastructure has become non-negotiable. Implementing strong security measures—such as complex passwords, multi-factor authentication, and comprehensive data encryption—is essential to building a solid defense.
However, these controls alone are not enough. Organizations must proactively leverage thorough security testing services —including vulnerability scanning, penetration testing, and ethical hacking—to identify and remediate hidden vulnerabilities before attackers exploit them. By embedding security testing into their processes, enterprises can strengthen their overall security posture, reduce risk, maintain regulatory compliance, and protect their brand reputation in an increasingly hostile cyber landscape.
Security testing is not just a technical task but a strategic investment that empowers businesses to operate safely, confidently, and resiliently in the digital age.
Discover more