Recommended Blogs

API Security Testing: A Step-by-Step Guide
Table of Content
- What is API Security Testing?
- Things to Know About APIs
- Common API Security Risks
- Preparing for API Security Testing
- What Are the Most Common API Security Vulnerabilities?
- Best Practices for API Security Testing
- Why is API Security Testing important and its benefit?
- Types of API security testing
- Steps to Follow for API Security Testing
- Which API Security Testing Tools Should Businesses Use?
- Best Practices for API Security Testing
- Conclusion
- How Can TestingXperts Help with API Security Testing?
In today’s interconnected world, where the flow of information and data between applications is constant, the security of APIs has become a pressing concern. With cyber threats growing in sophistication and frequency, the importance of API security testing cannot be ignored. This is where API security testing becomes essential to ensure the confidentiality, integrity, and availability of sensitive data and resources.
What is API Security Testing?
API Security Testing is a crucial component of ensuring the robustness and integrity of APIs. Application Programming Interfaces act as the bridge between different software systems, enabling seamless data exchange. However, they can also become vulnerable entry points for cyber threats if not adequately secured. API Security testing solutions involve systematically assessing APIs for potential vulnerabilities and implementing measures to protect against unauthorized access, data breaches, injection attacks, and other security risks.
Through comprehensive testing, organizations can proactively identify and address security loopholes in their APIs. It evaluates authentication and authorization mechanisms, input validation techniques, error handling practices, rate limiting, and other critical aspects. By leveraging advanced tools, methodologies, and industry best practices, API Security Testing helps organizations fortify their APIs and safeguard sensitive data and resources.
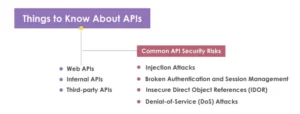
Things to Know About APIs
Application Programming Interfaces are protocols, tools, and definitions that facilitate communication between software applications. They define how different software components should interact, allowing developers to access specific functionalities or data from external systems or services. APIs enable integration, automation, and collaboration between diverse applications, ultimately enhancing user experiences and enabling the seamless flow of information.
Various types of APIs are:
Web APIs:
They enable communication between web-based applications, allowing developers to access data and functionalities over the internet using standard web protocols such as HTTP and REST.
Internal APIs:
Also known as private or enterprise APIs, these are designed for internal use within an organization. They enable different teams or systems to interact and share data securely.
Third-party APIs:
They are provided by external service providers, allowing developers to access their platform’s functionalities or data. Examples include payment gateways, social media APIs, and mapping services.
Common API Security Risks
Despite their benefits, APIs can be vulnerable to various security risks. Some common vulnerabilities include:
Injection Attacks:
APIs can be vulnerable to injection attacks, where malicious code or commands are injected into API requests. This can lead to unauthorized data exposure, compromised systems, or a takeover.
Broken Authentication and Session Management:
Weak authentication mechanisms, improper session handling, or inadequate access controls can expose APIs to authentication and session-related vulnerabilities. Attackers may exploit these weaknesses to impersonate legitimate users, hijack sessions, or gain unauthorized access to sensitive data.
Insecure Direct Object References (IDOR):
APIs that expose internal references, such as database IDs or file paths, without proper authorization checks can be prone to IDOR vulnerabilities. Attackers can manipulate these references to access unauthorized resources or sensitive information.
Denial-of-Service (DoS) Attacks:
APIs can be targeted with DoS attacks, where attackers overwhelm the API infrastructure with a flood of requests, rendering the API unresponsive or unavailable. This disrupts services, impacts user experience, and potentially leads to financial losses.
Preparing for API Security Testing
Ensuring the security of APIs is crucial to protect sensitive data and prevent potential breaches. API security testing plays a vital role in identifying vulnerabilities and weaknesses in API implementations.
The following are some pointers to consider when preparing for API security testing:
Setting up the Testing Environment
Establishing a robust testing environment that closely resembles the production environment is essential. Here are key considerations:
Isolate the Testing Environment:
Create a separate, isolated environment dedicated explicitly to API security testing. This prevents any accidental impact on the production systems and ensures a controlled testing environment.
Replicate Production Configuration:
Replicate the configuration of the production environment as closely as possible, including the server setup, network architecture, and infrastructure components. This ensures that the security tests accurately reflect real-world scenarios.
Utilize Virtualization or Containerization:
Leverage virtualization technologies like virtual machines or containerization platforms (e.g., Docker) to create a scalable and reproducible testing environment. This enables the easy setup of multiple testing instances and facilitates efficient testing of different API configurations.
Identifying the Scope of Testing
Defining the scope of API security testing is vital to ensure focused efforts and comprehensive coverage. Consider the following factors:
APIs and Endpoints:
Determine which APIs and specific endpoints will be included in the testing. It’s essential to consider internal and external-facing APIs and any public APIs that may expose sensitive data or critical functionalities.
Authentication and Authorization Mechanisms:
Assess the APIs’ various authentication and authorization mechanisms. Include scenarios like API keys, tokens, or user credentials to evaluate the security measures thoroughly.
Data Validation and Input Handling:
Analyze how APIs handle data validation and input handling. Assess how they respond to input formats, including invalid or unexpected data. Pay special attention to potential injection vulnerabilities.
Error Handling and Exception Management:
Evaluate how APIs handle errors and exceptions. Test their response to different error conditions and ensure that sensitive information is not leaked in error messages.
Gathering Necessary Tools and Resources
Equipping your API security testing efforts with the right tools and resources is essential for effective testing. Consider the following:
API Testing Tools:
Explore and select appropriate API testing tools that support security testing, such as OWASP ZAP, Burp Suite, or Postman. These tools offer features like vulnerability scanning, fuzz testing, and API traffic interception for comprehensive testing.
Security Testing Frameworks:
Familiarize yourself with security testing frameworks, such as the OWASP API Security Top 10, which guides the most critical API security risks. These frameworks serve as invaluable references throughout the testing process.
Documentation and Specifications:
Obtain the API documentation, specifications, and relevant security requirements. Thoroughly review them to understand the expected behavior, expected security measures, and any specific test cases.
Security Testing Checklist:
Develop a comprehensive security testing checklist encompassing various aspects of API security, including authentication, authorization, input validation, error handling, and encryption. This checklist will serve as a roadmap for your testing efforts.
What Are the Most Common API Security Vulnerabilities?
Although APIs make applications more flexible, they also open doors to new attacks if the security box is left unchecked. According to Salt Security’s 2025 State of API Security Report, 99% of organisations said they encountered API-security issues in the last 12 months. Let’s take a look at the common API security vulnerabilities that teams need to know to strengthen their systems by eliminating the weak points:
- SQL Injection in APIs: This occurs when user-supplied data is passed into a database query without proper validation or sanitization. Attackers manipulate these inputs to retrieve, modify, or delete sensitive data.
- Broken Authentication in APIs: This occurs when login mechanisms or token handling are poorly implemented, resulting in vulnerabilities that can be exploited. Attackers then impersonate legitimate users or gain unauthorized access to restricted endpoints. Weak password policies, improper session management, or insecure token storage are the primary causes of this issue.
- Insecure Direct Object References (IDOR): This vulnerability appears when an API exposes internal identifiers directly, allowing users to access resources that shouldn’t be accessible. Attackers then modify IDs in requests to view or manipulate the data of other users.
- Insufficient Rate Limiting: Without proper rate limits, APIs become vulnerable to brute-force attacks, credential stuffing, or automated abuse. Attackers overwhelm systems by sending excessive traffic, which can lead to performance issues or unauthorized access attempts. This vulnerability is widespread in public or widely integrated APIs.
- Excessive Data Exposure: APIs often return more data than necessary, assuming that the client will filter out the data it does not need. Attackers can exploit this by analyzing responses for sensitive fields that should not be visible. This issue often arises from the use of generic endpoints for convenience.
Want to understand which vulnerabilities matter most for your industry? Talk to our API security experts.
Best Practices for API Security Testing
Effective API security testing is crucial for building a resilient system that ensures seamless integration and interoperability. The following are some of the best practices for API security testing that help catch vulnerabilities early to avoid costly breaches:
- Embed API Security in the DevOps Pipeline to ensure vulnerabilities are caught early rather than after deployment.
- Utilize automated API security testing tools to quickly and consistently identify common issues.
- Input validation is one of the most fundamental practices for preventing injection attacks and data corruption.
- Consistent authentication and authorization checks ensure only intended users access sensitive resources.
- Comprehensive logging and monitoring make it easier to detect anomalies, ongoing attacks, or misuse.
Why is API Security Testing important and its benefit?
APIs are the heart of many applications, providing developers with powerful interfaces to the services an organization has to offer. Ensuring that APIs are conformant to published specifications and are resilient to bad and potentially malicious input is critical to an organization’s overall security.
Traditional dynamic application security testing (DAST) scanners cannot cover APIs completely; they cover only a small portion of them. If an organization’s front end does not interact with all API endpoints, traditional DAST scanners will miss them. It is therefore essential to adopt a modern, dynamic API security testing strategy that targets issues in all an API’s endpoints.
What are the benefits of using API security testing?
At the most basic level, API security testing helps identify and prevent vulnerabilities and their associated potential organizational risk.
Specifically, API security testing is fine-tuned to both the API being tested and an organization’s overall strategy and best practices. API scanners work at a deeper level, examining the APIs that power single-page web apps, IoT devices, or mobile apps. By understanding what an API expects as input, API scanners can intelligently fuzz data to uncover hidden bugs.
Types of API security testing
• Static Analysis Security Testing (SAST)
• Dynamic Application Security Testing (DAST)
• Software Composition Analysis (SCA)
• Authentication
• Authorization
Steps to Follow for API Security Testing
As the importance of robust API security continues to grow, organizations must conduct thorough and systematic security testing to identify vulnerabilities and mitigate risks.
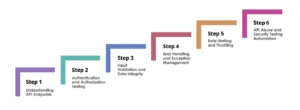
Following are the steps to follow when implementing API security testing:
Step 1: Understanding API Endpoints
API endpoints serve as the entry points for interactions with an API. To conduct effective security testing:
Define API Endpoints:
Identify and document all API endpoints. Categorize them based on functionality, sensitivity, and potential security risks.
Identify Sensitive Endpoints and Vulnerabilities:
Determine which endpoints handle sensitive data, perform critical operations, or involve user authentication. These endpoints may be more prone to security vulnerabilities and require rigorous testing.
Map API Endpoints:
Create a comprehensive map of API endpoints, including the request and response types, expected behavior, and associated security controls. This map will serve as a reference during testing to ensure thorough coverage.
Step 2: Authentication and Authorization Testing
Authentication and authorization mechanisms play a vital role in securing APIs. When testing, consider the following:
Evaluate Authentication Effectiveness:
Assess the strength and effectiveness of authentication mechanisms, such as API keys, tokens, or multifactor authentication. Verify that only authenticated users can access protected resources.
Examine Authorization Controls:
Test the authorization controls to ensure only authorized users or roles can perform specific actions. Pay attention to privilege escalation risks, such as bypassing authorization checks or gaining unauthorized access to sensitive data.
Test for Improper Access Controls:
Identify potential security misconfigurations or improper access controls that may allow unauthorized access to sensitive endpoints or operations. Thoroughly examine access control rules and configurations.
Step 3: Input Validation and Data Integrity
Proper input validation is crucial for preventing injection attacks and maintaining data integrity. During testing:
Analyze Input Validation Techniques:
Evaluate how the API handles input validation to prevent common vulnerabilities like SQL injection, Cross-Site Scripting (XSS), or XML External Entity (XXE) attacks. Test for both expected and unexpected input scenarios.
Ensure Data Integrity:
Verify that the API performs proper validation, sanitization, and encoding of user-supplied data to prevent data corruption or tampering. Validate the integrity of data transmitted between the client and server.
Test for Data Leakage and Exposure Risks:
Identify potential data leakages risks, such as inadvertently disclosing sensitive information in responses or error messages. Test for scenarios where sensitive data may be unintentionally exposed.
Step 4: Error Handling and Exception Management
Proper error handling and exception management improve an API’s overall security and robustness. When conducting testing:
Assess Error Handling Mechanisms:
Evaluate how the API handles errors and exceptions. Test for proper error codes, informative messages, and appropriate logging practices.
Test for Information Disclosure Vulnerabilities:
Look for potential information disclosure vulnerabilities in error responses or stack traces. Ensure that error messages do not expose sensitive information that could aid attackers.
Evaluate Exception Management Practices:
Assess how the API handles unexpected situations, such as unhandled exceptions or denial-of-service attacks. Verify that the API gracefully handles exceptions and does not expose system vulnerabilities.
Step 5: Rate-limiting and Throttling
Rate limiting and throttling mechanisms protect APIs against abuse and denial-of-service attacks. During testing:
Understand the Importance of Rate Limiting:
Recognize the significance of rate limiting and throttling to prevent abuse, brute-force attacks, or DoS scenarios. Familiarize yourself with industry best practices.
Test for Bypassing Rate Limits:
Attempt to bypass rate limits and verify if the API enforces them consistently. Check for potential vulnerabilities that allow attackers to circumvent rate limits and overload the system.
Verify Effectiveness of Rate-limiting Mechanisms:
Test the API under various load conditions to ensure that rate-limiting and throttling mechanisms function as expected. Measure the API’s response time and stability during high-volume traffic.
Step 6: API Abuse and Security Testing Automation
Leverage automation testing techniques for API security testing to maximize efficiency and coverage. When testing, consider the following:
Explore Techniques to Identify and Prevent API Abuse:
Learn about common API abuse scenarios, such as parameter tampering, replay attacks, or API key exposure. Develop test cases to identify and mitigate these risks.
Implement Automated Security Testing:
Utilize automated tools and frameworks, such as OWASP ZAP or Burp Suite, to streamline security testing efforts. Automate vulnerability scanning, fuzz testing, cyber insider and security checks to achieve comprehensive coverage.
Leverage Tools and Frameworks:
Leverage open-source tools and frameworks tailored for API security testing. These resources provide a wealth of knowledge, best practices, and test scripts to enhance the effectiveness of your testing efforts.
Which API Security Testing Tools Should Businesses Use?
Selecting compatible API security testing tools is critical to ensure consistent protection across the API structure. Let’s take a look at some of the commonly used tools across industries:
OWASP ZAP
- An open-source tool that scans APIs for common vulnerabilities.
- Offers passive and active testing modules.
- Driven by community and regularly updated with new security rules.
- Integrates seamlessly with CI/CD environments for continuous testing.
Postman API Security Features
- Known for its API development and testing capabilities.
- Users can run security checks directly and automate scans through scripts.
- Helps validate authentication flows, input handling, and endpoint behavior.
- An easy-to-access interface makes security testing more accessible.
Burp Suite
- Professional-grade tool designed for deep manual and automated API security analysis.
- Its scanner can detect injection flaws, misconfigurations, and authentication weaknesses.
- Offers extensible and detailed reporting.
Nessus
- Focuses on vulnerability scanning across networks, servers, and APIs.
- Helps locate misconfigurations and missing patches.
- Offers comprehensive reporting to prioritize remediation efforts.
Tools identify risks, but expertise determines impact. Many teams struggle with false positives, weak configurations, and CI/CD integration. With deep API security testing and DevSecOps experience, TestingXperts helps businesses turn tool findings into actionable fixes, ensuring APIs stay secure without slowing down releases.
Best Practices for API Security Testing
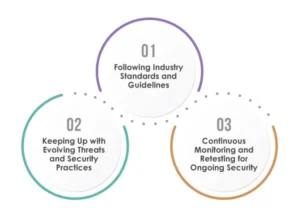
To achieve robust security, it’s crucial to follow best practices that align with industry standards, stay updated on evolving threats, and adopt continuous monitoring and retesting:
Following Industry Standards and Guidelines:
To ensure robust API security, it is vital to follow industry standards and guidelines. These standards provide a framework for implementing adequate security controls and mitigating common vulnerabilities. By adhering to these standards, organizations can align their security practices with industry best practices and reduce the risk of potential breaches.
Keeping Up with Evolving Threats and Security Practices:
It is another critical aspect of API security. The threat landscape constantly evolves, with new attack vectors and techniques emerging regularly. Staying updated on the latest threats allows organizations to identify and address vulnerabilities proactively before they can be exploited. By actively participating in security communities, attending conferences, and leveraging threat intelligence sources, organizations can stay one step ahead of attackers and implement timely security measures.
Continuous Monitoring and Retesting for Ongoing Security:
These are essential for maintaining ongoing security. It is not enough to perform security testing once and consider the job done. APIs and their associated threats evolve. Organizations can detect and respond to potential security incidents in real-time by implementing continuous monitoring. Additionally, regular retesting helps identify new vulnerabilities that may have been introduced due to system updates or changes in the threat landscape. This iterative approach ensures that APIs remain secure and protected against emerging risks.
Conclusion
API security testing is crucial to safeguard the integrity, availability, and confidentiality of data exchanged through APIs. Organizations can identify and address vulnerabilities in their APIs by following a comprehensive step-by-step guide. As technology evolves, staying updated and adapting security practices is essential to ensure robust API security.
How Can TestingXperts Help with API Security Testing?
At TestingXperts, we understand the significance of API security testing and offer comprehensive solutions to help organizations identify and mitigate potential risks. Our experienced team of testers and security professionals specializes in API security testing, utilizing industry-leading tools and methodologies. Our services include:
Comprehensive API Security Assessments:
Our experts perform in-depth vulnerability assessments of your APIs, examining all critical components for potential vulnerabilities. We thoroughly analyze authentication and authorization mechanisms, input validation techniques, error-handling practices, and rate-limiting mechanisms.
Realistic Testing Environment:
We create a controlled testing environment that simulates real-world scenarios while minimizing the impact on your live systems. This ensures accurate assessments without disrupting your production environment.
Customized Scope and Coverage:
We work closely with you to define the scope of testing based on your specific requirements. Our team examines all relevant API endpoints and functionalities, leaving no loophole in identifying potential vulnerabilities.
Automation for Efficiency:
We use cutting-edge automation tools and frameworks to enhance testing efficiency and coverage. This allows us to conduct comprehensive assessments while reducing manual effort and maximizing accuracy.
Whether it’s setting up the testing environment, conducting thorough assessments, or providing actionable remediation strategies, TestingXperts can assist you in ensuring the security of your APIs. Contact us today to learn more about our API security testing services and how we can support your organization.
FAQs
The three main types of API testing are functional, performance, and security testing. Functional testing checks if the API works as expected, performance testing assesses speed and scalability, and security testing identifies vulnerabilities to protect against cyber threats.
API security is ensured by implementing authentication (OAuth, JWT), encryption (TLS/SSL), rate limiting, input validation, and regular security testing. Following secure coding practices and using API gateways help prevent unauthorized access and data breaches.
API security testing can be incorporated into your DevOps pipeline by using automated security testing tools like OWASP ZAP during the CI/CD process. This integration helps identify security vulnerabilities early in the development cycle, reducing the risk of vulnerabilities in production.
Focus on common security issues such as authentication flaws, broken access controls, and injection vulnerabilities like SQL injection. Additionally, testing for cross-site scripting (XSS), improper encryption, and ensuring robust input validation are essential to keep your APIs secure.
Automated security tests are effective at detecting common privilege escalation issues but might struggle with more complex vulnerabilities. While tools can validate access controls and permissions, complex edge cases or advanced attacks may require additional manual testing or custom scripts to uncover.
Ensure compliance by testing that APIs handle personal data securely through encryption, anonymization, and strict access controls. Testing should verify that sensitive data is properly stored and transmitted, with no leaks that could violate data privacy regulations like GDPR.
Discover more